Know Your Enemy: What Happens Behind the Scenes in a DDoS Attack
 Originally published on February 07, 2017 by Kimberley Parsons Trommler
Originally published on February 07, 2017 by Kimberley Parsons Trommler
Last updated on January 23, 2024
•
29 minute read
This is part 1 of a new blog series about DDoS attacks. This article covers the different types of DDoS attacks and how they work. You'll learn the main categories of DDoS attacks and which vulnerabilities each one takes advantage of.
Additional articles will cover how to mitigate DDoS attacks and will give you insight into how Paessler recently defended ourselves against a DDoS.
What Would You Like to Know?
What are DDoS Attacks?
Definition: What are Denial of Service Attacks?
Denial of Service attacks (shortened to "DoS") are a class of attacks where the attacker attempts to cripple an online service so badly that valid users can no longer use the service. The goal is not to steal data, but to take a website or online service out of action. The ultimate goal is to exhaust all of your resources (e.g. bandwidth or CPU) so that you can't serve your customers anymore.
While most online attacks are meant to either steal sensitive information or to install malicious software, DoS attacks do not attempt to breach your IT security defenses. Rather, they make your website or services unusable for valid users. DoS attacks are very visible, since all users are affected.
Most DoS attacks are carried out by hacktivists, vandals or extortionists in an attempt to harm your organization by causing loss of revenues, loss of reputation, and loss of customer trust. Depending on how long a DoS attack lasts (days, weeks or months) it can cause very significant financial damage and long-term loss of reputation.
What's the difference between DoS and DDoS?
DoS:
A DoS (Denial of Service) attack is launched from a single device with a single Internet connection. Since a single machine can't flood a web service with traffic alone, it usually tries to exploit a software vulnerability or flood a target with fake requests, in an attempt to exhaust the resources of a server (e.g. use up all the CPU). If the attacker can bind up enough of the server resources, the target will become so slow that the service is unusable and will eventually crash.
DoS attacks are usually carried out using scripts or DoS tools which are (unfortunately) freely available on the Internet. As such, the barriers-to-entry for running a DoS attack are very low.
DDoS:
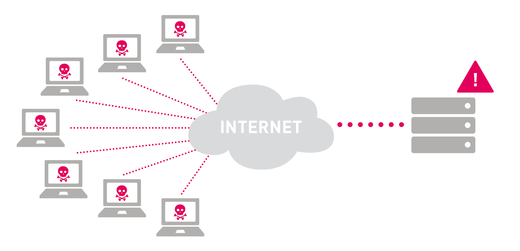
A DDoS (Distributed Denial of Service) attack is launched from multiple connected devices simultaneously, from different parts of the Internet. All of these devices attack a single target at the same time, usually with the goal of generating so much traffic that bandwidth to the target is completely saturated, so that valid customer traffic doesn't get through. It's much more difficult to defend yourself against these multi-device attacks due to the sheer volume of traffic involved.
Executing a DDoS attack requires control of multiple Internet-connected devices. These devices can be PCs, tablets, smart phones, surveillance cameras, or any other Internet-connected device. The devices have been compromised ahead of time by malware which is used to control the devices from a central point. A group of devices that are under the control of an attacker is called a botnet.
When the attacker activates the botnet, all of the devices in the botnet will start to attack the same target at the same time. The attacker can control which and how many devices will attack the target and for how long.
Building up a botnet requires enough hacking skills to compromise a large numbers of devices and to create the centralized software to control all of them. However, there are also botnets "for hire", which will execute custom DDoS attacks, for a price. These DDoS-for-hire services are also known as "booters" or "stressers" and range from $10-$300, depending on the length of the attack and the number of bots attacking concurrently.
DDoS attacks are usually high-traffic events, measured in Gbps (gigabits per second) or PPS (packets per second). 20-40 Gbps is usually enough to shut down most network infrastructures. The large Mirai botnet attacks in late 2016 against Brian Krebs' "Krebs on Security" website and against Dyn's DNS services reached over 665 Gpbs and 1.2 Tbps respectively, the largest known to date.
What Classes of DDoS Attacks Are There?
DDoS attacks can be grouped into three main types of attacks:
1) Volume-based attacks
2) Protocol attacks
3) Application layer attacks
Volume-Based DoS Attacks
The goal of volume-based attacks is to saturate the bandwidth at the attacked site. Attacks in this category include UDP flooding, ICMP flooding and packet-spoofing.
Volume based attacks are measured in bits per second (Bps).
Protocol DoS Attacks
Protocol attacks consume server resources, with the goal of consuming so many resources that the server no longer responds to valid requests. Protocol attacks may also attack intermediate devices such as firewalls and load balancers. Attacks in this category include SYN flooding, fragmented packets, "ping of death", smurf attacks and fraggle attacks.
Protocol attacks are measured in packets per second (PPS).
Application Layer DoS Attacks
Application layer attacks, also known as "Layer 7 attacks", attempt to overload a server by sending a very large number of requests that require resource-intensive handling and processing. This category includes HTTP flooding, DNS query flooding and "slow" attacks such as Slowloris or R.U.D.Y.
Application layer attacks are measured in the number of requests per second (RPS). It only takes 50-100 RPS to effectively cripple a mid-sized website.
What Types of DDoS Attacks Are There?
UDP Flooding
In a UDP flood attack, the attacker uses the User Datagram Protocol (UDP), a standard part of the TCP/IP protocol stack, to flood random UDP ports on the target host. The host then needs to check for an application listening on that port, and, if no application is found, to reply with an ICMP Destination Unreachable packet. This constant, repeated checking and answering consumes resources on the target host until it becomes inaccessible.
ICMP (ping) Flooding
In this type of attack, the attacker sends ICMP Echo Request packets (also known as "ping") packets to the target host. The attacker sends packets as fast as possible without waiting for the host to reply, which fills up both incoming and outgoing bandwidth to that host. The host becomes inaccessible because valid traffic can't get through to the host, and even if it does, the host is busy attempting to respond to the ping with Echo Reply packets.
SYN Flooding
SYN flooding abuses the TCP three-way handshake, which is used to establish a TCP connection between two machines.
Normally, in the first part of the handshake, machine A sends a "SYN" (synchronization) request to machine B, requesting that a connection be established. Machine B then responds with a "SYN-ACK" (synchronization acknowledgement) that it's willing to establish the connection. Machine A then sends an "ACK" (acknowledgement) that it has received the SYN-ACK, and the connection is then established.
In a SYN flood attack, the attacker sends the target host a high number of SYN requests, but doesn't respond to the SYN-ACKs. The target host reserves resources for each half-open connection, waiting for the ACK which never comes. Eventually, all resources are reserved, and no new connections can be made.
In a version of the SYN flood attack, the attacker spoofs (fakes) the source IP addresses in the SYN requests, so that the target sends its SYN-ACK replies to a large number of uninvolved machines, which then drop the SYN-ACKs. The effect on the target is the same: it holds half-open connections open, waiting for ACKs which will never arrive. However, spoofing the source IP addresses hides the IP address of the attacker, making it more difficult to simply block or drop the incoming SYNs.
Ping of Death
A Ping of Death (POD) attack uses malicious or malformed pings to a target host. The maximum length of an IP packet is 65535 bytes (including the header), while the underlying layer 2 Data Link layer usually imposes a smaller maximum frame size. Ethernet, for example, has a maximum frame size of 1500 bytes.
In normal operation, the larger IP packet would be split up into multiple, smaller Ethernet frames, sent across the network, and re-assembled at the other end. This process is known as IP fragmentation and is a perfectly normal occurrence in data networks.
In a ping-of-death attack, however, the individual fragments are manipulated so that the re-assembled packet ends up being larger than 65535 bytes. This can then cause buffer overflows on the target, causing a denial of service for valid packets to that host.
HTTP Flooding
Similar to other flooding attacks, HTTP flooding involves sending valid HTTP GET or HTTP POST requests to a web server. But you send HTTP requests that force the web server to reserve resources for that request. If the attacker can send enough HTTP requests to exhaust all of the server's resources, then the service is unavailable for valid users.
Slowloris
The Slowloris attack allows a web server to focus an attack on another server, without affecting other services or ports on the target network. It thus allows a very focused attack on one specific server. Slowloris makes multiple connections to the target server and holds those connections open for as long as possible. It opens a connection to the target server but sends only partial HTTP requests, without ever completing a request fully, forcing the target to keep the connections open. Eventually the target server can't accept any more connections from valid clients.
R.U.D.Y.
R.U.D.Y. stands for R-U-Dead-Yet?, a slow-rate HTTP POST attack which causes a DoS by abusing long form field submissions to a web server. It injects only a single byte of information into an application's POST field at a time and then waits, thereby forcing the application threads to wait for the end of never-ending posts. The web server must behave this way to support valid users with slow connections. R.U.D.Y. opens multiple, simultaneous connections which eventually exhausts the server's connection table, leading to DoS for legitimate users.
Reflection Attacks
There are two very different kinds of cyber-attacks that are both called "reflection attacks": Authentication Reflection and DDoS Reflection. The two use very different methods:
Authentication Reflection is not a type of DDoS. Rather, it is a type of man-in-the-middle attack, where the attacker attempts to convince both sides of a transaction that they're talking to each other, while they're actually both talking to the attacker. This type of attack involves the attacker "reflecting" authentication information back to the valid users.
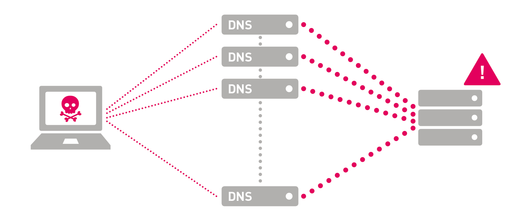
A DDoS Reflection does not involve any authentication processes. Rather, it spoofs IP addresses to trick other machines into generating traffic to the target. For example, the attacker will spoof the source IP address in a DNS request, using the target's IP address instead of his own. The DNS server will then respond to the request by sending the response to the target. Using this method, the attacker has "reflected" the response to the target.
If the attacker can get enough servers to reflect responses to the target, it will overwhelm the target.
Reflection attacks are most often used together with amplification, which is the next type of attack in the list.
Amplification Attacks
There are multiple types of DDoS attacks that rely on "amplification" to increase the size and thus damage of an attack. Many of these rely on publicly available servers that offer UDP-based services, such as DNS and NTP, so you'll often see these attacks under the names "DNS amplification" or "NTP amplification".
However, amplification attacks are certainly not limited to DNS and NTP: they can also be performed using public servers for SNMPv2, NetBIOS, SSDP, CharGEN, QOTD, BitTorrent, Kad, Quake Network Protocol, Steam Protocol, RIPv1, Multicast DNS (mDNS), Portmap/RPC and LDAP.
All UDP-based amplification attacks abuse a characteristic of UDP: UDP does not validate source IP addresses. As such, it is very easy to forge the IP addresses to include any arbitrary IP address as the source. To attack a specific target, you use the target's IP address as the spoofed source IP address for (otherwise valid) requests to a public server.
Using DNS as an example, the attacker would send DNS requests to multiple public DNS servers, using the target's IP address as the source IP. All of these DNS servers then respond to the target, overwhelming the target.
Some of the UDP protocols respond to certain commands with responses that are much, much larger than the original request. So, the attacker can send relatively small requests to the servers, which will then respond with very large amounts of data to the target. So, a single packet from the attacker can result in tens or hundreds of times the bandwidth in the response. This is the "amplification" part of the attack: the public server amplifies the size of the attack on behalf of the attacker.
Different protocols have different amplification factors. You can see why NTP, in particular, is popular for this type of DDoS.
| Protocol | Bandwidth Amplification Factor |
Vulnerable Command |
|---|---|---|
|
DNS |
28 to 54 | see: TA13-088A |
|
NTP |
556.9 | see: TA14-013A |
|
SNMPv2 |
6.3 | GetBulk request |
|
NetBIOS |
3.8 | Name resolution |
|
SSDP |
30.8 | SEARCH request |
|
CharGEN |
358.8 | Character generation request |
|
QOTD |
140.3 | Quote request |
|
BitTorrent |
3.8 | File search |
|
Kad |
16.3 | Peer list exchange |
|
Quake Network Protocol |
63.9 | Server info exchange |
|
Steam Protocol |
5.5 | Server info exchange |
|
Multicast DNS (mDNS) |
2 to 10 | Unicast query |
|
RIPv1 |
131.24 | Malformed request |
|
Portmap (RPCbind) |
7 to 28 | Malformed request |
|
LDAP |
46 to 55 | Malformed request |
What are White Hat and Black Hat Attacks?
Not all attacks against IT infrastructure are malicious! "White hat" hackers are people who own a website or service and who want to test their IT defenses. They run an attack against their own infrastructure to ensure that the measures they've put into place are actually effective.
"Black hat" hackers, on the other hand, do have malicious intent.
So, DoS attacks and tools such as stressers can be used for both good and bad intent.
Who Carries Out DDoS Attacks, and Why?
The goal of most DDoS attacks is to harm the target organization: to cause them financial harm, loss of revenues, loss of reputation and loss of customer trust. Most are carried out against a specific company or service, to damage that one company.
Some are motivated mainly by the wish to harm a specific organization, due to political or ideological beliefs:
- Hacktivisim
- Vandalism
- Personal rivalry
- Cyberwarfare
although some are purely financially motivated:
- Extortion/ransom
- Business competition
- DDoS-for-hire
and a few are carried out simply to claim bragging rights in the hacker community.
Occasionally a DDoS attack is performed only as a smokescreen, to distract the organization while the carrying out a stealthier attack simultaneously. One example is the Bank of the West, where thieves used a DDoS attack to distract the bank while stealing $900000 from a customer account.
Sources of DDoS Attacks: Where are they coming from?
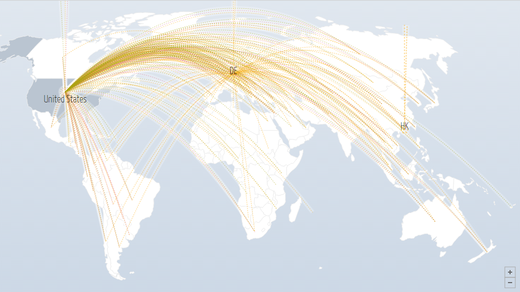
The machines being used to carry out the attacks are spread around the world. Digital Attack Map shows DDoS attacks that are happening right now, in real-time, including their main source and target. As you'll see on this map, both the sources and targets are worldwide. Not surprisingly, more developed areas (with a higher concentration of PC users) also appear more often as both source and target.
It is extremely difficult to track down the source of a DDoS attack, and most attackers remain anonymous. Most attacks end up attributed to criminal hackers or foreign governments, and there's no shortage of conspiracy theories about them. Law enforcement is sometimes able to track down the hackers, but usually only catch the more inexperienced "script kiddies", not the brains behind the botnets.
More important than the source of the attack is what you can do to defend yourself, which will be covered in the next part of this series.
Want to know more?
Here are some interesting links with more information about DDoS attacks:
- Imperva's DDoS 101 -- A Beginners Guide to DDoS
- Radware's DDoSPedia -- Comprenensive List of DDoS Attacks
- Top 10 Booters -- Example List of Stressers/Booters
- the guardian's Discussion of the Mirai Botnet-Based DDoS Attacks Against Dyn
- US CERT's Alert TA14-017A about UDP-based Amplification Attacks
- Brainstuff's Why Do People Perform DDoS Attacks?
- Coreo on Law Enforcement and DDoS Attacks
Previous articles from Paessler about DDoS: